Choosing Your Book Security Tags: Key Specs to Compare in 2025
Introduction: Navigating the Global Market for book security tags
In today’s increasingly digital world, the challenge of safeguarding physical assets remains critical, particularly for libraries, bookstores, and educational institutions. Sourcing effective book security tags is essential for preventing theft and ensuring inventory management, making it a priority for B2B buyers across diverse regions, including Africa, South America, the Middle East, and Europe. This guide offers a comprehensive overview of various types of book security tags, including RFID, electromagnetic (EM) strips, and Tattle-Tape systems, providing insights into their applications, benefits, and best practices for implementation.
Navigating the global market for book security tags can be complex, given the wide range of suppliers and products available. This guide empowers international B2B buyers by outlining critical factors such as supplier vetting processes, cost considerations, and the technological advantages of different tagging systems. By understanding these elements, buyers can make informed decisions that enhance security and operational efficiency within their organizations.
Whether you are looking to upgrade existing security measures or implement new systems, this guide serves as a valuable resource to help you navigate the intricacies of sourcing book security tags tailored to your specific needs.
Understanding book security tags Types and Variations
| Type Name | Key Distinguishing Features | Primary B2B Applications | Brief Pros & Cons for Buyers |
|---|---|---|---|
| RFID Tags | Wireless communication, data storage capability, high durability | Libraries, bookstores, publishers | Pros: Efficient inventory management, real-time tracking. Cons: Higher initial investment. |
| Tattle-Tape Strips | Thin, adhesive strips, easy to apply, discreet | Libraries, educational institutions | Pros: Cost-effective, reliable theft deterrent. Cons: Limited reusability, may require detuning process. |
| EM Book Tags | Ultra-thin, adhesive, can be turned on/off, archival quality | Libraries, archives, book retailers | Pros: Effective concealment, reusable. Cons: Requires specific systems for activation. |
| Security Cases | Lockable cases for DVDs and books, sturdy design | Libraries, media rental shops | Pros: Physical protection, prevents theft. Cons: Higher cost, less flexibility. |
| Detuning Cards | Used to deactivate security tags, simple design | Libraries, bookstores | Pros: Easy to use, affordable. Cons: Only functional when paired with other security systems. |
What Are RFID Tags and How Do They Benefit B2B Buyers?
RFID (Radio Frequency Identification) tags are advanced security tools that enhance inventory management through wireless communication. These tags store essential information about each book, such as title and author, which can be read by RFID readers. Their durability and ability to track multiple items simultaneously make them suitable for libraries and bookstores aiming to streamline operations. However, the initial investment can be higher compared to traditional security methods, making it essential for buyers to evaluate long-term benefits versus upfront costs.
How Do Tattle-Tape Strips Function in Book Security Systems?
Tattle-Tape strips are thin, adhesive security strips designed for easy application within books. Their discreet nature makes them a popular choice among libraries and educational institutions looking to deter theft without compromising aesthetics. While Tattle-Tape offers a cost-effective solution, it is less reusable than other options and may require a detuning process upon checkout, which could lead to operational inefficiencies if not managed properly.
What Makes EM Book Tags a Viable Choice for Libraries and Retailers?
EM (Electromagnetic) book tags are ultra-thin, adhesive security tags that can be easily concealed within book pages. They can be turned on and off, allowing for reuse while maintaining their effectiveness over time. This makes them particularly suitable for libraries and archives that prioritize both security and the preservation of materials. However, buyers should consider the need for compatible activation systems, which could add to the overall cost of implementation.
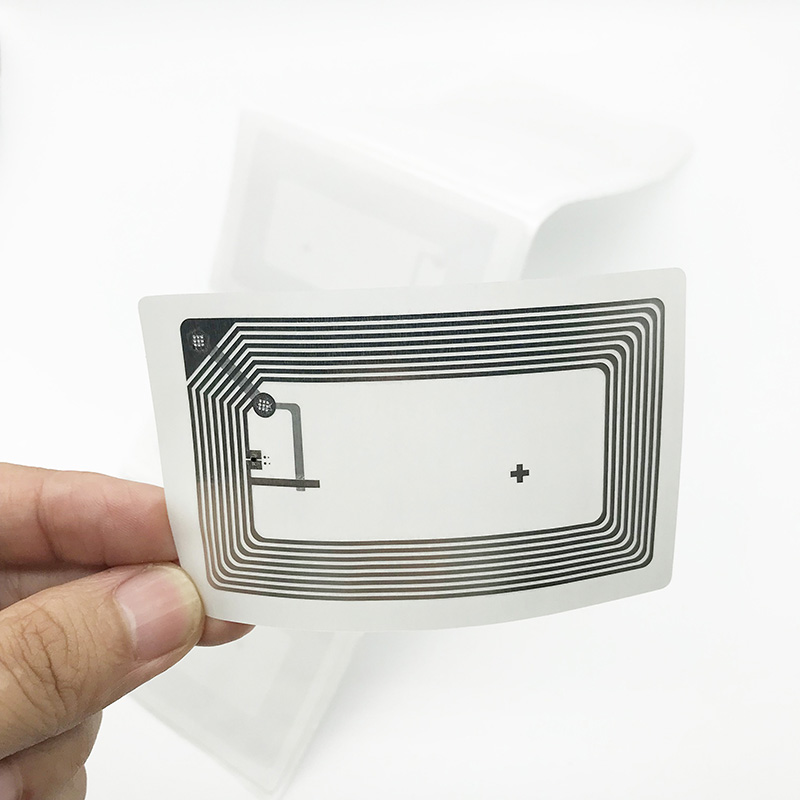
Illustrative image related to book security tags
Why Should Businesses Consider Security Cases for Book Protection?
Security cases provide a physical barrier against theft, especially for high-value items like DVDs and rare books. Their sturdy design allows them to withstand tampering, making them an excellent choice for libraries and media rental shops. Despite their effectiveness, the higher costs associated with security cases may deter some buyers. It’s crucial for businesses to weigh the benefits of physical protection against their budget and operational needs.
How Do Detuning Cards Support Book Security Systems?
Detuning cards are essential tools used to deactivate security tags, ensuring that patrons can check out items without triggering alarms. Their simple design and low cost make them a practical addition for libraries and bookstores. However, they function best when integrated with a comprehensive security system, meaning buyers should consider how these cards fit into their overall security strategy.
Key Industrial Applications of book security tags
| Industry/Sector | Specific Application of Book Security Tags | Value/Benefit for the Business | Key Sourcing Considerations for this Application |
|---|---|---|---|
| Libraries | RFID tags for tracking inventory and circulation | Enhanced operational efficiency and reduced theft | Compliance with ISO standards, durability, and ease of installation |
| Retail Bookstores | EM security strips for theft prevention | Protection of high-value inventory and reduced losses | Compatibility with existing security systems, cost-effectiveness |
| Educational Institutions | Tattle-Tape for securing textbooks | Minimization of book loss and improved resource management | Adhesive quality, ease of application, and removal process |
| Publishing Houses | RFID tags for inventory and distribution tracking | Streamlined operations and better stock management | Customization options, data retention capabilities |
| Museums and Archives | Security tags for rare book collections | Preservation of valuable assets and enhanced security | Non-invasive application methods, archival quality materials |
How Are Book Security Tags Used in Libraries to Enhance Operations?
In libraries, RFID tags are employed to streamline inventory management and track book circulation effectively. By embedding these tags within books, libraries can conduct real-time inventory checks and quickly locate misplaced items. This technology minimizes human error, allowing staff to focus on customer service rather than manual inventory processes. For international buyers, particularly in regions with varying library infrastructure, sourcing RFID tags that comply with local regulations and standards is crucial.

Illustrative image related to book security tags
What Role Do EM Security Strips Play in Retail Bookstores?
In retail bookstores, electromagnetic (EM) security strips are vital for safeguarding inventory against theft. These strips are discreetly placed within books, triggering alarms if an item is taken without proper checkout. This application not only protects high-value items but also fosters a secure shopping environment for customers. Buyers should consider sourcing strips that are easy to install and compatible with existing security systems to optimize their investment.
How Do Educational Institutions Benefit from Tattle-Tape Security?
Educational institutions utilize Tattle-Tape security strips to protect textbooks and other educational materials from theft. This approach not only minimizes losses but also ensures that resources remain available for students. The ease of application and removal of Tattle-Tape is essential for schools that frequently update their collections. When sourcing these products, institutions should prioritize high-quality adhesive materials that do not damage books, especially in diverse climates across Africa and South America.
How Can Publishing Houses Improve Stock Management with RFID Tags?
Publishing houses are increasingly adopting RFID tags to enhance inventory tracking and distribution processes. These tags allow for efficient stock management, enabling quick identification of available titles and reducing the time spent on manual checks. For B2B buyers in Europe and the Middle East, it’s important to select RFID solutions that offer customization options and robust data retention capabilities, ensuring that the technology evolves with the business needs.
Why Are Security Tags Essential for Museums and Archives?
Museums and archives often utilize security tags to protect rare and valuable book collections. These tags help in monitoring the movement of items within and outside the facility, thus preserving cultural heritage. For international buyers, sourcing tags that can be applied non-invasively and are made from archival-quality materials is essential to prevent damage to priceless artifacts. Proper sourcing ensures that the integrity of the collection is maintained while enhancing security measures.
3 Common User Pain Points for ‘book security tags’ & Their Solutions
Scenario 1: Ineffective Theft Prevention Measures
The Problem: Many libraries and bookstores face significant losses due to theft, which can severely impact their operational budgets. A B2B buyer might discover that existing security tags are either too easy to remove or ineffective in deterring would-be thieves. As a result, they experience frequent inventory discrepancies, leading to frustration among staff and a loss of trust from patrons. This situation can escalate, especially in environments where high-value or rare books are present.

Illustrative image related to book security tags
The Solution: To enhance theft prevention, it is crucial to invest in high-quality security tags that have proven effectiveness. Consider sourcing advanced RFID tags or EM (Electromagnetic) security strips that are designed for optimal concealment and durability. For instance, the bibliotheca Tattle-Tape™ or EM Book Tags can offer robust protection against theft while being discreet enough not to detract from the aesthetics of the books. Additionally, integrating these tags with an automated security system can significantly reduce theft incidents. Training staff on how to effectively monitor and manage inventory using these tags will also help maintain stock integrity.
Scenario 2: Difficulty in Managing Inventory Efficiently
The Problem: Efficient inventory management is a persistent challenge for libraries and bookstores, particularly for those with large collections. A B2B buyer may struggle with the time-consuming process of tracking books, leading to delays in restocking and a poor user experience for patrons. Moreover, traditional systems may result in human errors, creating discrepancies that can complicate inventory audits.
The Solution: Implementing RFID technology can revolutionize how inventory is managed. RFID tags allow for bulk scanning, enabling staff to count and locate books much faster than manual methods. For a more seamless integration, B2B buyers should look for RFID tags that are compliant with industry standards, such as ISO 18000-3 mode 1. These tags can store essential book information and can be updated as needed, facilitating real-time inventory management. Furthermore, pairing RFID tags with inventory management software can streamline operations, reduce errors, and enhance service delivery to patrons. Regular training sessions for staff on using RFID systems can also improve efficiency and accuracy.
Scenario 3: Compatibility Issues with Existing Security Systems
The Problem: Libraries and bookstores often face compatibility challenges when integrating new security tags with their existing systems. A buyer might find that newly purchased security tags do not work effectively with their current EM or RFID systems, leading to wasted resources and time. This misalignment can result in increased costs as they attempt to troubleshoot or replace incompatible equipment.
Illustrative image related to book security tags
The Solution: To mitigate compatibility issues, it is vital to conduct thorough research before making purchases. B2B buyers should ensure that any new security tags are compatible with existing systems by consulting with suppliers about technical specifications and system requirements. It is advisable to opt for a unified system that offers both security tags and readers designed to work together seamlessly. Additionally, establishing a relationship with a supplier that provides ongoing support and updates can help ensure that the technology remains compatible as systems evolve. Regular audits of security systems can also identify potential compatibility issues before they become problematic.
Strategic Material Selection Guide for book security tags
What Are the Common Materials Used for Book Security Tags?
In the realm of book security tags, selecting the right material is crucial for ensuring durability, effectiveness, and compliance with international standards. Here, we analyze four common materials used in book security tags, focusing on their properties, advantages, disadvantages, and specific considerations for international B2B buyers.
How Does Polyethylene Contribute to Book Security Tags?
Polyethylene (PE) is a widely used plastic in the production of book security tags due to its lightweight and flexible nature. It exhibits excellent chemical resistance and is suitable for various environmental conditions, making it a popular choice for libraries in diverse climates.
Pros: PE is cost-effective and easy to manufacture, allowing for mass production of tags. Its flexibility ensures that tags can be seamlessly integrated into various book formats without damaging the materials.
Cons: While PE is durable, it may not withstand extreme temperatures or prolonged exposure to UV light, which can lead to degradation over time. This limitation may affect the longevity of the tags in harsh environments.

Illustrative image related to book security tags
Impact on Application: Polyethylene tags are compatible with most book types and can be used in both hardcover and paperback formats. However, their performance in high-temperature regions may require additional protective measures.
Considerations for International Buyers: Buyers from regions like Africa and South America should ensure that PE tags comply with local environmental regulations. Understanding the local climate can also guide the decision on whether to use PE or consider alternatives.
What Role Does PVC Play in Book Security Tags?
Polyvinyl Chloride (PVC) is another prevalent material for book security tags, known for its robustness and durability. PVC is resistant to moisture, chemicals, and abrasion, making it suitable for environments where books may be exposed to various elements.
Pros: The durability of PVC ensures a longer lifespan for security tags, reducing the need for frequent replacements. Additionally, PVC can be produced in various colors and finishes, allowing for customization.
Cons: The production of PVC can be more complex and costly compared to other materials, which may impact overall pricing for bulk orders. Additionally, PVC is less environmentally friendly, raising concerns about sustainability.
Impact on Application: PVC tags are ideal for high-traffic libraries and environments where books are frequently handled. Their durability makes them suitable for both public and academic libraries.
Considerations for International Buyers: Buyers in Europe, particularly Germany, may face stricter regulations regarding PVC use due to environmental policies. Understanding compliance with standards such as REACH (Registration, Evaluation, Authorisation, and Restriction of Chemicals) is essential.
How Do RFID Tags Enhance Book Security?
Radio Frequency Identification (RFID) tags offer a technological advancement in book security, utilizing radio waves for tracking and inventory management. These tags are typically made from a combination of plastic and electronic components.
Pros: RFID tags improve operational efficiency by enabling quick inventory checks and precise tracking of book locations. They can store extensive data, enhancing library management systems.

Illustrative image related to book security tags
Cons: The initial investment for RFID systems can be high due to the technology involved. Additionally, RFID tags may require specialized readers, which can complicate implementation.
Impact on Application: RFID tags are particularly beneficial for large libraries and bookstores, enabling efficient management of extensive collections. However, their effectiveness may be diminished in environments with high electromagnetic interference.
Considerations for International Buyers: Buyers should assess the compatibility of RFID technology with existing systems and ensure compliance with international standards such as ISO 18000-3. This is particularly relevant for libraries in Europe and the Middle East.
What Are the Benefits of Tattle-Tape Security Strips?
Tattle-Tape, a brand of electromagnetic (EM) security strips, is designed specifically for library applications. Made from a composite of plastic and metal, these strips are thin and easily integrated into books.
Pros: Tattle-Tape strips are discreet and do not compromise the aesthetic of books. They are also reusable, allowing for cost savings over time.
Cons: While effective, Tattle-Tape may require a specific deactivation tool, which can add to operational complexity. Additionally, their effectiveness can be reduced if not properly installed.
Impact on Application: These strips are suitable for all types of books and are particularly effective in preventing theft in libraries.
Considerations for International Buyers: Buyers should ensure that Tattle-Tape products meet local security standards and are compatible with existing library security systems.
Summary Table of Material Options for Book Security Tags
| Material | Typical Use Case for book security tags | Key Advantage | Key Disadvantage/Limitation | Relative Cost (Low/Med/High) |
|---|---|---|---|---|
| Polyethylene (PE) | General library use | Cost-effective and flexible | Limited temperature resistance | Low |
| Polyvinyl Chloride (PVC) | High-traffic libraries | Durable and customizable | Higher production cost and environmental concerns | Med |
| RFID Tags | Large libraries and bookstores | Efficient inventory management | High initial investment and complexity | High |
| Tattle-Tape Strips | Libraries for theft prevention | Discreet and reusable | Requires specific deactivation tools | Med |
By carefully considering these materials and their properties, international B2B buyers can make informed decisions that align with their operational needs and compliance requirements.
In-depth Look: Manufacturing Processes and Quality Assurance for book security tags
What Are the Key Stages in the Manufacturing Process of Book Security Tags?
The manufacturing of book security tags involves several critical stages, each contributing to the final product’s quality and effectiveness. Understanding these stages helps B2B buyers make informed decisions when selecting suppliers.
Material Preparation: What Materials Are Used in Book Security Tags?
The first stage in manufacturing book security tags is material preparation. Common materials include:
- Polymeric Films: These are used for the outer layer of RFID tags and security strips, providing durability and flexibility.
- Electromagnetic Strips: Found in EM tags, these strips are essential for theft prevention and are made from specific metal alloys.
- Adhesives: High-quality adhesives are crucial for ensuring that tags remain securely attached to books without damaging them.
Suppliers often source materials from reputable vendors to ensure compliance with international quality standards. This selection process is vital, as the quality of raw materials directly affects the performance and longevity of the tags.

Illustrative image related to book security tags
How Are Book Security Tags Formed and Assembled?
Once materials are prepared, the next step is forming and assembly. This phase typically involves:
- Die-Cutting: For tags like Tattle-Tape or RFID, die-cutting machines create precise shapes and sizes, ensuring uniformity across batches.
- Embedding Chips: In RFID tags, microchips are embedded into the tags during the assembly process. This is a delicate task, as any misalignment can affect functionality.
- Adhering Strips: EM tags require precise placement of electromagnetic strips between layers to ensure they are effective while remaining discreet.
Automation plays a significant role in this stage, helping to maintain consistency and reduce production costs.
What Finishing Techniques Are Commonly Used in Book Security Tags?
Finishing techniques are essential for enhancing the durability and aesthetic appeal of book security tags. Common practices include:
- Coating: A protective coating is applied to RFID tags to enhance water and scratch resistance.
- Printing: Customization options such as branding or barcodes are printed on the surface, adding functionality and brand recognition.
- Quality Checks: Before packaging, tags undergo visual inspections to ensure there are no defects.
These finishing techniques ensure that the tags not only perform well but also meet the branding needs of libraries and bookstores.
What Quality Assurance Measures Are Necessary for Book Security Tags?
Quality assurance (QA) is critical in the manufacturing of book security tags. Implementing robust QA measures helps ensure that products meet international standards and customer expectations.

Illustrative image related to book security tags
Which International Standards Should B2B Buyers Be Aware Of?
For book security tags, compliance with international standards is essential. Key standards include:
- ISO 9001: This standard outlines requirements for a quality management system, ensuring that suppliers consistently provide products that meet customer and regulatory requirements.
- CE Marking: Required for products sold within the European Economic Area, CE marking indicates that the product meets EU safety, health, and environmental protection standards.
- ISO/IEC 18000-3: This standard specifically relates to RFID technology, ensuring that tags operate effectively and are interoperable with various systems.
Understanding these standards helps B2B buyers assess the credibility of suppliers and the safety of their products.
What Are the Key Quality Control Checkpoints in the Manufacturing Process?
Quality control (QC) checkpoints are critical for maintaining product integrity. Common QC stages include:
- Incoming Quality Control (IQC): This involves inspecting raw materials upon arrival to ensure they meet specified standards before production begins.
- In-Process Quality Control (IPQC): During manufacturing, regular checks are conducted to monitor processes and identify any deviations from quality standards.
- Final Quality Control (FQC): Once production is complete, a final inspection is conducted to ensure that the finished products meet all specifications before packaging and shipping.
These checkpoints help to catch defects early and ensure that only high-quality products reach the market.
How Can B2B Buyers Verify Supplier Quality Control?
For international B2B buyers, verifying a supplier’s quality control measures is essential to ensure reliability and compliance with standards.

Illustrative image related to book security tags
What Methods Can Be Used to Evaluate Supplier Quality Control?
- Supplier Audits: Conducting site visits to suppliers allows buyers to evaluate their manufacturing processes, quality control systems, and adherence to standards firsthand.
- Quality Reports: Requesting detailed quality reports can provide insights into the supplier’s QC processes, historical performance, and any corrective actions taken.
- Third-Party Inspections: Engaging third-party inspection services can offer an unbiased assessment of the supplier’s quality control measures and product compliance.
By utilizing these methods, B2B buyers can ensure they partner with suppliers who prioritize quality and reliability.
What Are the Challenges in Quality Control for International B2B Buyers?
International buyers may face specific challenges in verifying quality control measures:
- Language Barriers: Communication difficulties can lead to misunderstandings regarding quality requirements.
- Regulatory Differences: Different countries have varying standards and regulations, which can complicate compliance verification.
- Logistical Issues: Long shipping times may delay the identification of quality issues, making it harder to address problems promptly.
To navigate these challenges, buyers should establish clear communication channels and consider working with local representatives or agents familiar with the market.
Conclusion: Ensuring Quality in Book Security Tags Manufacturing
In summary, the manufacturing processes and quality assurance measures for book security tags are essential for ensuring product efficacy and compliance with international standards. B2B buyers must be proactive in understanding these processes, verifying supplier capabilities, and maintaining quality throughout their supply chain. By focusing on these areas, businesses can enhance their operational efficiency and safeguard their assets against theft, ultimately leading to increased customer satisfaction.
Practical Sourcing Guide: A Step-by-Step Checklist for ‘book security tags’
Introduction
When sourcing book security tags, it’s essential for B2B buyers to have a structured approach to ensure they choose the right products that align with their security needs and operational goals. This checklist provides a step-by-step guide to help you navigate the complexities of procuring book security tags effectively, ensuring you make informed decisions that will enhance your asset protection strategy.
1. Identify Your Security Needs
Begin by assessing the specific security challenges your library or bookstore faces. Consider factors such as the types of materials you need to secure (e.g., hardcover books, DVDs) and the level of theft you experience. This step is critical as it lays the foundation for your procurement strategy and helps in selecting the most suitable security tags.
2. Define Your Technical Specifications
Clearly outline the technical requirements for the security tags you need. This includes determining whether you require RFID tags, electromagnetic (EM) strips, or a combination of both. Each type has distinct features:
– RFID Tags: Offer advanced tracking and inventory management capabilities.
– EM Strips: Provide a cost-effective solution for basic security needs.
Understanding these specifications will help you communicate effectively with suppliers and ensure compatibility with existing systems.
3. Research Potential Suppliers
Conduct thorough research to identify reputable suppliers of book security tags. Look for companies with a proven track record in your region, particularly those that specialize in library security solutions. Key factors to consider include:
– Product range and availability.
– Customer reviews and testimonials.
Evaluating suppliers at this stage can prevent future procurement issues and ensure you partner with reliable sources.
4. Request Samples for Evaluation
Before finalizing your order, request samples from shortlisted suppliers to evaluate the quality and effectiveness of the tags. Testing the samples in your environment will allow you to assess how well they perform in real-world conditions. Pay attention to:
– Adhesive strength and durability.
– Ease of application and removal.
This hands-on approach will help you make a more informed choice.

Illustrative image related to book security tags
5. Verify Compliance and Certifications
Ensure that the security tags meet industry standards and compliance requirements. Check for certifications such as ISO compliance, which indicates adherence to quality and safety standards. Compliance is crucial not only for security effectiveness but also for maintaining trust with your patrons.
6. Compare Pricing and Terms
Obtain detailed quotes from multiple suppliers and compare pricing structures, including bulk discounts and shipping costs. Be sure to consider payment terms and warranty options as well. A comprehensive comparison will help you identify the best value for your investment while ensuring you do not compromise on quality.
7. Establish a Support and Maintenance Plan
Once you’ve selected your supplier, discuss support and maintenance options. Inquire about after-sales support, availability of replacement tags, and any additional services they offer, such as installation assistance or training for staff. Having a solid support plan ensures that you can address any issues that arise post-purchase, maintaining the integrity of your security system.
By following this checklist, B2B buyers can streamline their procurement process for book security tags, ensuring a secure and efficient library or bookstore environment.
Comprehensive Cost and Pricing Analysis for book security tags Sourcing
What Are the Key Cost Components in Sourcing Book Security Tags?
When sourcing book security tags, understanding the cost structure is essential for B2B buyers. The main components of the cost include:
- Materials: The choice of materials directly impacts pricing. For instance, RFID tags generally require higher-quality materials compared to electromagnetic (EM) strips, which can affect durability and performance.
- Labor: Labor costs can vary based on the complexity of the manufacturing process. Tags that require intricate designs or additional features, such as customization, will incur higher labor costs.
- Manufacturing Overhead: This encompasses indirect costs such as utilities, rent, and equipment depreciation. A manufacturer with advanced technology and efficient processes may offer lower overhead costs.
- Tooling: Initial setup and tooling costs can be significant, especially for custom tags. Buyers should consider these costs when negotiating prices for smaller orders or customized solutions.
- Quality Control (QC): Ensuring the reliability of security tags is critical, particularly for libraries and retailers. Manufacturers that implement rigorous QC processes may charge more, but this often results in better performance and fewer defects.
- Logistics: Shipping costs can fluctuate based on the order size, weight, and distance. International buyers must factor in these costs, which can significantly impact the total price.
- Margin: Suppliers typically include a profit margin in their pricing. Understanding the standard margins in your industry can help in negotiations.
How Do Volume and Customization Affect Pricing for Book Security Tags?
Pricing for book security tags is influenced heavily by volume and customization. Higher order quantities often lead to lower per-unit costs due to economies of scale. Manufacturers may offer attractive pricing tiers, so it’s beneficial for buyers to assess their needs and order strategically.
Customization, on the other hand, can increase costs. Custom designs or specific functionalities (like special adhesive properties) require additional resources and may lead to longer lead times. Buyers should weigh the benefits of customization against potential cost increases.
What Other Factors Impact the Pricing of Book Security Tags?
Several additional factors play a role in pricing:
- Materials and Quality Certifications: Tags made from premium materials or those that meet specific quality certifications (like ISO standards) can command higher prices. Buyers should ensure that the quality aligns with their security requirements.
- Supplier Reputation: Established suppliers with a track record of reliability may charge more due to their reputation and the quality assurance they provide.
- Incoterms: Understanding Incoterms is crucial for international transactions. They define the responsibilities of buyers and sellers regarding shipping, insurance, and tariffs, which can affect the total cost.
What Tips Can Help Buyers Negotiate Better Prices for Book Security Tags?
To achieve cost-efficiency in sourcing book security tags, consider the following negotiation tips:
- Understand Total Cost of Ownership (TCO): Evaluate not just the purchase price but also the lifetime cost associated with maintenance, potential replacements, and operational efficiencies. This broader perspective can inform better purchasing decisions.
- Leverage Volume Discounts: When possible, consolidate orders to meet minimum order quantities (MOQs) that unlock volume discounts. This can significantly reduce overall costs.
- Build Relationships: Establishing a good rapport with suppliers can lead to better pricing and service. Long-term partnerships often result in favorable terms and priority during peak times.
- Research Market Prices: Stay informed about market trends and competitor pricing. This knowledge can empower you during negotiations and help you identify fair pricing structures.
Conclusion: Understanding Pricing Nuances for International Buyers
For international B2B buyers, particularly in regions like Africa, South America, the Middle East, and Europe, understanding the nuances of sourcing book security tags is vital. Factors such as regional logistics, tariffs, and local supplier capabilities can affect pricing. It’s advisable to conduct thorough market research and engage with multiple suppliers to secure the best deal.

Illustrative image related to book security tags
Disclaimer: Prices mentioned in this analysis are indicative and may vary based on current market conditions, supplier negotiations, and specific buyer requirements. Always consult with suppliers for the most accurate and updated pricing information.
Alternatives Analysis: Comparing book security tags With Other Solutions
When considering security solutions for libraries and bookstores, it’s essential to evaluate various alternatives to book security tags. These alternatives not only differ in technology but also in performance, cost, and operational impact. By understanding these options, international B2B buyers can make informed decisions that align with their security needs and budget constraints.
| Comparison Aspect | Book Security Tags | RFID Technology | Surveillance Systems |
|---|---|---|---|
| Performance | Effective for deterring theft; requires manual checks for inventory | High efficiency in tracking and managing inventory; real-time updates | Provides visual monitoring and recording; can deter theft through visibility |
| Cost | Moderate initial cost; ongoing costs for maintenance | Higher initial investment; potential cost savings in labor over time | Variable costs depending on the number of cameras and installation fees |
| Ease of Implementation | Simple to apply and integrate into existing systems | Requires more extensive setup and staff training | Installation can be complex; may require professional services |
| Maintenance | Minimal maintenance; occasional replacement needed | Moderate maintenance; requires software updates and hardware checks | Ongoing maintenance for camera systems and software management |
| Best Use Case | Libraries with low to moderate theft rates | Large libraries or bookstores with high inventory turnover | High-risk areas needing constant surveillance and monitoring |
What Are the Advantages and Disadvantages of RFID Technology Compared to Book Security Tags?
RFID technology offers a sophisticated alternative to traditional book security tags. Its primary advantage is the ability to track inventory in real-time, allowing for simultaneous scanning of multiple items, which significantly reduces the time and labor required for inventory management. This technology also enhances the user experience by providing accurate information about item availability. However, the upfront costs and the need for staff training can be prohibitive for smaller libraries or bookstores.

Illustrative image related to book security tags
How Do Surveillance Systems Compare to Book Security Tags in Terms of Security Solutions?
Surveillance systems, including CCTV and motion detectors, provide a different layer of security. Their primary advantage lies in visual monitoring, which can deter potential thieves by their mere presence. They can also record events for later review, aiding in investigations. However, surveillance systems typically involve higher installation and maintenance costs, and they do not actively prevent theft like security tags do. For businesses in high-risk areas, the combination of surveillance and security tags may provide the most robust solution.
Conclusion: How Can B2B Buyers Choose the Right Security Solution?
When selecting a security solution, B2B buyers should consider several factors, including the specific security needs of their library or bookstore, the budget available for both initial investment and ongoing maintenance, and the operational complexities involved in implementation. A thorough assessment of theft rates, inventory management needs, and available resources will guide buyers in choosing the most suitable option. Whether opting for book security tags, RFID technology, or surveillance systems, aligning the chosen method with the organization’s overall security strategy is crucial for long-term success.
Essential Technical Properties and Trade Terminology for book security tags
What Are the Essential Technical Properties of Book Security Tags?
When selecting book security tags for libraries, bookstores, or educational institutions, understanding the technical specifications is crucial. Here are the key properties to consider:
1. Material Composition
Most security tags are made from durable materials such as polyester or PVC, which provide resistance to wear and tear. The choice of material affects the tag’s longevity and effectiveness in preventing theft. B2B buyers should prioritize tags made from high-quality materials to ensure they withstand everyday handling without damage.
2. Adhesive Quality
The adhesive used in security tags must be archival quality, meaning it won’t damage the book or degrade over time. This is particularly important for libraries, where books are valuable assets. A strong adhesive ensures that tags remain securely in place, reducing the risk of loss or theft.
3. Frequency and Compatibility
Security tags often operate at specific frequencies, such as 125 kHz for electromagnetic (EM) tags or 13.56 MHz for RFID tags. Compatibility with existing security systems is essential for seamless integration. B2B buyers should verify that the tags meet their library or bookstore’s existing systems to avoid additional costs for upgrades.
4. Size and Design
The dimensions of security tags vary, with options like rectangular or square shapes. For example, RFID tags may come in sizes like 50 x 50 mm, while EM tags may have different shapes depending on their application. Selecting the right size ensures that tags fit well within the materials they protect, such as books or DVDs.
5. Read/Write Capability
RFID tags offer unique advantages, including the ability to store and update information. This dynamic feature allows libraries to manage inventory efficiently, providing real-time data about book availability. B2B buyers should consider RFID tags for improved operational efficiency and enhanced customer service.
What Are Common Trade Terms Related to Book Security Tags?
Understanding industry terminology is vital for B2B transactions. Here are some common terms you might encounter:
1. OEM (Original Equipment Manufacturer)
This term refers to companies that produce parts or equipment that may be marketed by another manufacturer. In the context of security tags, OEM suppliers provide tags that can be branded and sold by libraries or bookstores, allowing for customization.
2. MOQ (Minimum Order Quantity)
MOQ defines the smallest number of units a supplier is willing to sell. This term is essential for buyers to understand as it impacts inventory management and initial investment. Buyers should negotiate MOQs that align with their purchasing capacity.

Illustrative image related to book security tags
3. RFQ (Request for Quotation)
An RFQ is a standard business process where a company requests pricing information from suppliers. For book security tags, issuing an RFQ allows buyers to compare prices and terms from different manufacturers, ensuring they receive the best deal.
4. Incoterms (International Commercial Terms)
These are predefined commercial terms published by the International Chamber of Commerce (ICC) that outline the responsibilities of buyers and sellers in international transactions. Understanding Incoterms helps B2B buyers clarify shipping responsibilities, costs, and risks when purchasing security tags from overseas suppliers.
5. SKU (Stock Keeping Unit)
An SKU is a unique identifier for a specific product, allowing for efficient inventory management. For book security tags, SKUs help businesses track different types and styles of tags, simplifying the ordering process and stock control.
Understanding these technical properties and trade terms will empower B2B buyers to make informed decisions when procuring book security tags. By prioritizing quality and comprehending industry language, businesses can enhance their security measures and operational efficiency.
Navigating Market Dynamics and Sourcing Trends in the book security tags Sector
What Are the Current Market Dynamics and Key Trends Influencing Book Security Tags?
The book security tags market is witnessing significant transformations driven by technological advancements and evolving consumer needs. Globally, the rise in library automation and digitization is a primary driver of demand for effective security solutions. RFID technology, in particular, has gained traction, offering enhanced tracking capabilities that simplify inventory management and improve user experience. International buyers, particularly from regions like Africa, South America, the Middle East, and Europe, are increasingly seeking integrated security solutions that combine RFID tagging with advanced surveillance systems. This trend is fueled by the growing emphasis on operational efficiency and loss prevention in libraries and bookstores.
Emerging B2B technology trends, such as the Internet of Things (IoT), are also influencing sourcing decisions. The integration of IoT-enabled devices allows for real-time monitoring of book inventory and security status, providing actionable insights for library management. Additionally, data analytics is becoming a vital component, enabling stakeholders to make informed decisions based on borrowing trends and inventory turnover rates. Buyers are looking for suppliers that offer comprehensive solutions, including installation, maintenance, and ongoing support, to ensure a seamless transition to modern security systems.
How Can B2B Buyers Address Sustainability and Ethical Sourcing in Book Security Tags?
As environmental awareness grows, sustainability is becoming a critical factor for B2B buyers in the book security tags sector. The production and disposal of security tags can have substantial environmental impacts, leading to increased scrutiny on sourcing practices. Buyers are encouraged to seek suppliers that prioritize eco-friendly materials and processes. For instance, some manufacturers are now using recycled materials in the production of RFID tags and security strips, reducing their carbon footprint.
Furthermore, ethical sourcing is paramount in establishing a responsible supply chain. Buyers should evaluate suppliers based on their adherence to fair labor practices and transparency in their sourcing methods. Certifications such as ISO 14001 for environmental management can serve as indicators of a supplier’s commitment to sustainability. By prioritizing suppliers that demonstrate a commitment to ethical practices and sustainability, B2B buyers can enhance their brand reputation while contributing to a more sustainable future.
What Is the Brief Evolution and History of Book Security Tags Relevant to B2B Buyers?
The evolution of book security tags began with traditional mechanical systems that utilized simple locking mechanisms. As libraries faced increasing challenges with theft and loss of materials, the need for more sophisticated solutions emerged. The introduction of electromagnetic (EM) tags revolutionized the industry, providing a reliable method for securing books without compromising accessibility.
The late 20th century saw the advent of RFID technology, which offered significant improvements over earlier systems. RFID tags allow for quick scanning and tracking of multiple items simultaneously, greatly enhancing inventory management and operational efficiency. Today, the market is characterized by a diverse range of products, including various types of RFID tags and security strips designed for different materials and formats, meeting the needs of modern libraries and bookstores. This historical context is essential for B2B buyers to understand the value proposition of contemporary security solutions and their relevance in today’s digital landscape.
Frequently Asked Questions (FAQs) for B2B Buyers of book security tags
-
How do I solve issues with book theft in my library or bookstore?
To address book theft effectively, consider implementing a combination of security tags, such as RFID tags or EM security strips. RFID tags provide real-time tracking and inventory management, while EM strips are effective in deterring theft when placed inside the book. Ensure staff is trained to recognize alarm triggers and conduct regular inventory checks. Additionally, consider installing security gates at exits to enhance protection against theft. Collaborating with suppliers for tailored solutions can further strengthen your security measures. -
What is the best type of security tag for protecting books?
The best type of security tag depends on your specific needs. RFID tags are ideal for comprehensive inventory management and quick scanning, making them suitable for libraries and bookstores with large collections. EM security strips are effective for straightforward theft prevention and are easy to install. For maximum protection, consider a hybrid approach that combines both RFID and EM technologies to ensure both efficient tracking and robust security. -
What should I consider when sourcing book security tags internationally?
When sourcing book security tags internationally, evaluate factors such as the supplier’s reputation, quality certifications, and compliance with international standards. Assess the supplier’s experience in your target market, particularly in regions like Africa, South America, the Middle East, and Europe. Additionally, consider logistical aspects such as shipping costs, delivery times, and customs regulations that may affect the import of security tags. It’s also essential to communicate clearly about your specific requirements and expectations. -
How can I vet potential suppliers for book security tags?
To vet potential suppliers, start by checking their credentials and industry reputation through reviews, testimonials, and case studies. Request samples to evaluate the quality of their products firsthand. Additionally, inquire about their manufacturing processes, quality assurance protocols, and compliance with safety standards. Engage in direct communication to assess their responsiveness and willingness to customize solutions for your specific needs. Establishing a solid relationship with your supplier can enhance trust and collaboration. -
What are the minimum order quantities (MOQ) for book security tags?
Minimum order quantities (MOQ) for book security tags can vary widely by supplier and product type. Generally, RFID tags may have higher MOQs due to the technology involved, often starting at 1,000 units. EM security strips may have lower MOQs, sometimes beginning at 500 units. Always clarify MOQ requirements with your supplier and explore options for bulk purchasing or gradual ordering to meet your inventory needs without overcommitting financially. -
What payment terms should I expect when purchasing book security tags?
Payment terms for purchasing book security tags can vary depending on the supplier and your relationship with them. Common practices include payment in full upfront, a deposit with the balance upon delivery, or net terms (e.g., net 30 or net 60 days). For international transactions, consider using secure payment methods such as letters of credit or escrow services to protect your investment. It’s essential to negotiate payment terms that align with your cash flow and financial strategy. -
How can I ensure quality assurance (QA) when sourcing book security tags?
To ensure quality assurance when sourcing book security tags, request detailed product specifications and certifications from the supplier. Implement a quality control process that includes inspecting samples before placing a large order. Establish clear communication regarding your quality expectations and any relevant industry standards. Additionally, consider arranging for third-party inspections or audits to verify the supplier’s compliance with quality assurance protocols throughout the production process. -
What logistics considerations should I keep in mind when importing book security tags?
When importing book security tags, logistics considerations include shipping methods, costs, lead times, and customs regulations. Choose a reliable freight forwarder experienced in handling similar products and regions. Be aware of import duties and taxes that may apply, which can affect overall costs. Ensure that all documentation, including invoices, packing lists, and certificates of origin, is accurate and complete to avoid delays at customs. Establish a clear timeline to manage expectations regarding delivery.
Top 7 Book Security Tags Manufacturers & Suppliers List
1. The Library Store – Library Security Supplies
Domain: thelibrarystore.com
Registered: 1996 (29 years)
Introduction: Library Security Supplies include various items designed to protect library materials and enhance security. Key products may include protective book covers, book repair supplies, circulation supplies such as book pockets and date due slips, bar code scanners, patron ID cards, and interlibrary loan products. Additional items may consist of label makers, label dispensers, and archival supplies for p…
2. Demco – Book Theft Prevention Solutions
Domain: demco.com
Registered: 1994 (31 years)
Introduction: Security & Traffic Control – Book Theft Prevention Products
3. Barnes & Noble – Security Tags
Domain: reddit.com
Registered: 2005 (20 years)
Introduction: Security tags are placed inside books at Barnes & Noble to prevent theft. They are designed to peel off easily without damaging the book, although some users report issues with residue or tearing pages. Tags are typically found in manga and hardcovers, often on the inside cover or blank pages. If a tag damages a book during removal, customers can exchange it at the store.
4. Bibliotheca – Tattle-Tape Security Strips
Domain: bibliotheca.com
Registered: 1998 (27 years)
Introduction: This company, Bibliotheca – Tattle-Tape Security Strips, is a notable entity in the market. For specific product details, it is recommended to visit their website directly.
5. Intrepid Security – RFID Book Tags & Library Security Systems
Domain: intrepidsecurity.com
Registered: 2000 (25 years)
Introduction: RFID Book Tags | Library Book Security Systems:
– Radio Frequency (RF) Book Security System: Entry-level system using RF antennas, ideal for school and college libraries. Protects books with an integrated RF label in a “book pocket”.
– RFID technology: Allows libraries to streamline borrowing processes with embedded RFID tags, enabling self-service kiosks for check-ins and check-outs.
– RFID St…
6. Brodart – RFID Tags
Domain: shopbrodart.com
Registered: 1999 (26 years)
Introduction: [{‘name’: ‘bibliotheca 2″ x 3″ Rectangle RFID Tag’, ‘item_number’: ‘WP-5120’, ‘price’: ‘$454.00’, ‘description’: ‘Long read range helps keep items secure’}, {‘name’: ‘RFID Tags™ fullDiscCD’, ‘item_number’: ‘WP-3698’, ‘price’: ‘$641.17’, ‘description’: ‘Longer read range for security and optimum productivity’}, {‘name’: ‘RFID Tag™ Square’, ‘item_number’: ‘WP-1497’, ‘price’: ‘$583.00’, ‘description’…
7. TAGIT – EM EAS Library Solutions
Domain: tagit-eas.ch
Introduction: EM EAS Library Solutions by TAGIT include invisible EM EAS tags (Tattle-Tape) for library book spines and CD/DVD EM EAS labels that detect even on metal surfaces. Key features include 3D detection for books and media, compatibility with various systems (3M, Sentry, Certus, etc.), silent operation, and a range of systems from budget-friendly to premium versions. TAGIT systems offer a 2-year warrant…
Strategic Sourcing Conclusion and Outlook for book security tags
How Can Strategic Sourcing of Book Security Tags Enhance Your Operations?
In the evolving landscape of library and bookstore management, the strategic sourcing of book security tags is paramount. By selecting high-quality solutions such as RFID tags and Tattle-Tape security strips, businesses can significantly bolster their theft prevention efforts while optimizing inventory management. The integration of advanced technologies not only streamlines operations but also enhances user experience, allowing for precise tracking and efficient stock management.
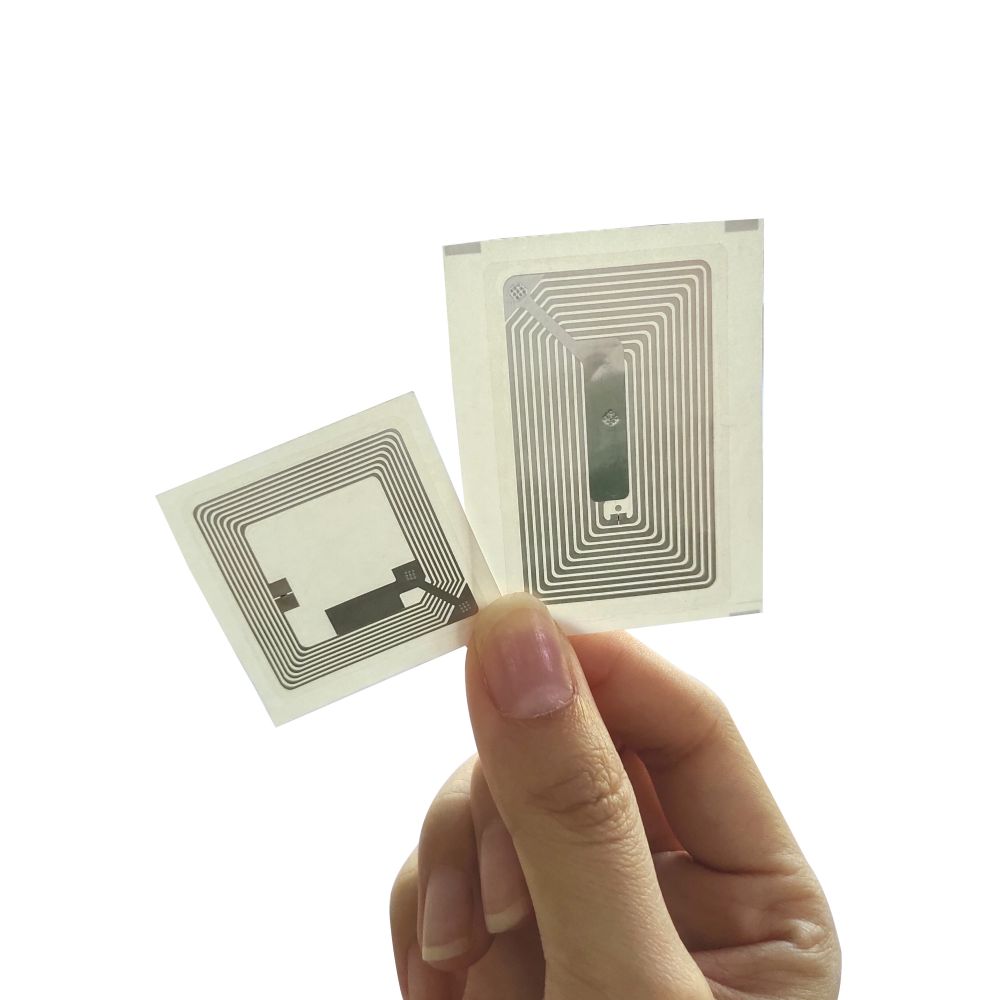
Illustrative image related to book security tags
For B2B buyers in Africa, South America, the Middle East, and Europe, it is crucial to evaluate suppliers who offer innovative and reliable security tag solutions tailored to your specific needs. The emphasis on compliance with international standards ensures that your investments are secure and effective.
As you consider your sourcing strategy, prioritize partnerships that provide comprehensive support and guidance, allowing you to navigate the complexities of security solutions with confidence. Embrace the future of library security by investing in top-tier products that will safeguard your assets and improve operational efficiency. Take the next step in securing your library or bookstore by exploring the latest offerings in book security tags today.
Important Disclaimer & Terms of Use
⚠️ Important Disclaimer
The information provided in this guide, including content regarding manufacturers, technical specifications, and market analysis, is for informational and educational purposes only. It does not constitute professional procurement advice, financial advice, or legal advice.
While we have made every effort to ensure the accuracy and timeliness of the information, we are not responsible for any errors, omissions, or outdated information. Market conditions, company details, and technical standards are subject to change.

Illustrative image related to book security tags
B2B buyers must conduct their own independent and thorough due diligence before making any purchasing decisions. This includes contacting suppliers directly, verifying certifications, requesting samples, and seeking professional consultation. The risk of relying on any information in this guide is borne solely by the reader.